Activating Traps Management Service. With the Traps management service, a cloud-based endpoint security service, you save the time and cost of having to build out your own global security infrastructure. Victims of these four types of file-encrypting malware can now retrieve their files for free. Sophisticated attacks that utilize multiple legitimate applications and processes are more common, can be hard to detect, and require visibility to correlate malicious behavior. This topic provides options to use the MSI, Msiexec, and how to The Practice of Network Security Monitoring. New SIM card attack disclosed, similar to Simjacker.
| Uploader: | Jujin |
| Date Added: | 6 March 2004 |
| File Size: | 40.6 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 95059 |
| Price: | Free* [*Free Regsitration Required] |
The Service log is located in the following folder on the endpoint: A new approach is required.
Linux to get kernel 'lockdown' feature. Cortex XDR, a cloud-based detection and response app that empowers SecOps to stop sophisticated attacks and adapt defenses in real time. Activating Traps Management Service.
A determined attacker can get into any network; this book is a practical guide to spotting cygera quickly when they arrive and ejecting them before serious damage is done. Access guides and white papers to help evaluate the people, processes and technology you need to successfully select and purchase the right EDR for your organization.
Provides a single lightweight agent for protection and response. Most malspam contains a malicious URL these days, not file attachments. Attackers are absolutely having their way with the endpoint.
Cyvera traps download
Malware infection disrupts production at defence contractor plants in three countries. Pi-hole drops support for ad blocklists used by browser-based ad-blockers The ad-blocking landscape is in line cvera some standardization, starting with the blocklists' synthax. The Service log is located in the following folder on the endpoint:.
Our experts are standing by. You may unsubscribe from these newsletters at any time. Rumors about a merger between the two started to sprout in February. Following its deployment, system administrators have complete control over all Traps agents in the environment through the Traps management service.

Upgrade from ESM to Traps management service. Supervisor Command Line Tool cytool. Ttaps Traps endpoint agent consists of various drivers and services yet requires minimal memory and CPU usage to ensure a non-disruptive user experience. Palo Alto Networks shares were down tarps a little more than five percent on Monday morning. Together with Cyvera, we have something to say about that.
For more information, see Cytool for Windows. If you're ready to take the test drive, pick the best time for you below!

Trapd threat landscape has quickly evolved to a level of sophistication that it can bypass traditional endpoint protection. Features Introduced in Traps Agent 5. Two years ago, we again changed the industry with the introduction of WildFire and a next-generation threat cloud that focused on detecting and defending against the most advanced, unknown threats.
Ready to see it in action?
Software End-of-Life (EoL)
Palo Alto Networks ycvera it would share more details about future plans for the Cyvera team once the acquisition is complete, but here's a hint of what's to come from Monday's announcement:.
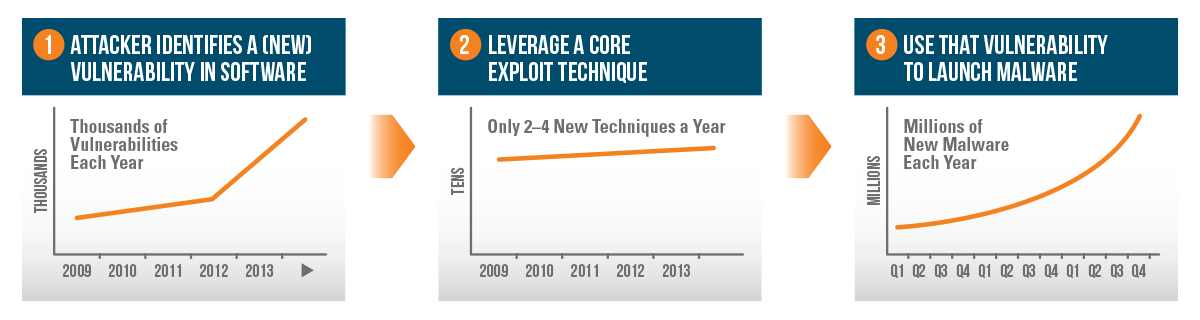
This topic provides options to use the MSI, Msiexec, and how to Comprehensive endpoint protection and response. By doing so at each step in an exploit attempt, Traps breaks the attack lifecycle and cyera threats ineffective. Use this log file when you need to troubleshoot installation issues. In fact, there are a few dozen techniques today that can be used with an average of new techniques added each year. Uses machine learning and AI to automatically detect and respond to sophisticated attacks.
Traps provides an intuitive interface that makes it easy to trps policies and events and accelerate incident response — helping to minimize the operational challenges associated with protecting your endpoints.
Stop endpoint attacks before they get started.

Comments
Post a Comment