But whatever the answer, a blocklist alone is not going to prevent BitTorrent users from running into trouble. A new paper published on these monitoring activities describes the variety of techniques being employed, and shows that P2P-blocklists offer little protection. You could write and find simpler scripts as well. For example, research has shown that due to shoddy techniques even a network printer can be accused of sharing copyrighted files on BitTorrent. I set it up and added the infringement list and was astonished when I started Deluge. The main point being: 
| Uploader: | Yorg |
| Date Added: | 24 March 2014 |
| File Size: | 66.37 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 64388 |
| Price: | Free* [*Free Regsitration Required] |
Years ago, when people had less understanding of these matters, blocklists seemed like the tool everyone needed. For those who still aren't convinced, think about how effective site-blocking is at preventing file-sharing. As soon as an order is handed down, sites can grab a new domain, a new IP address, or have infrinyement traffic funneled through any number of proxies and mirrors.
But whatever the answer, a blocklist alone is not going to prevent BitTorrent users from running into trouble. Their tracking machines can be shifted around IP addresses in the blink of an eye, through infringemwnt or even residential ISPs, if there is a real need for stealth. That's what binding the torrent client to the tap adapter blocklish. Try running Wireshark with Deluge running, see whether it is leaking.
For my years, some pirates have been putting their faith in so-called 'peer blocking' apps that aim to prevent anti-piracy agencies from connecting to their clients and monitoring their activities.
Unfortunately for those using them, these blocklists were completely ineffective and remain so infringemsnt. Network Connections Proxy Connections Blocklist The copyright infringement letter I received indicated the port number and it was notit was on one of the randomly generated ports: Now for the big non-surprise: I then changed the ports from random to specific ranges and asked my firewall to block all outgoing and incoming connections within those ranges Some anti-piracy groups are not recognized by the blocklist and therefore not blocked.
I have a custom script that goes into transmission's settings and binds IPv4 to the detected infrinhement address while disabling IPv6 with a loopback address. This means that users who rely on them as their only means of protection are at risk of being logged. Sign In or Register to comment. A new paper published on these monitoring activities describes the variety of techniques being employed, and blockliat that P2P-blocklists offer little protection. Over the past 18 years, ever since P2P blockllst made their run into the big time, users have been trying to figure out a way to avoid expensive lawsuits.
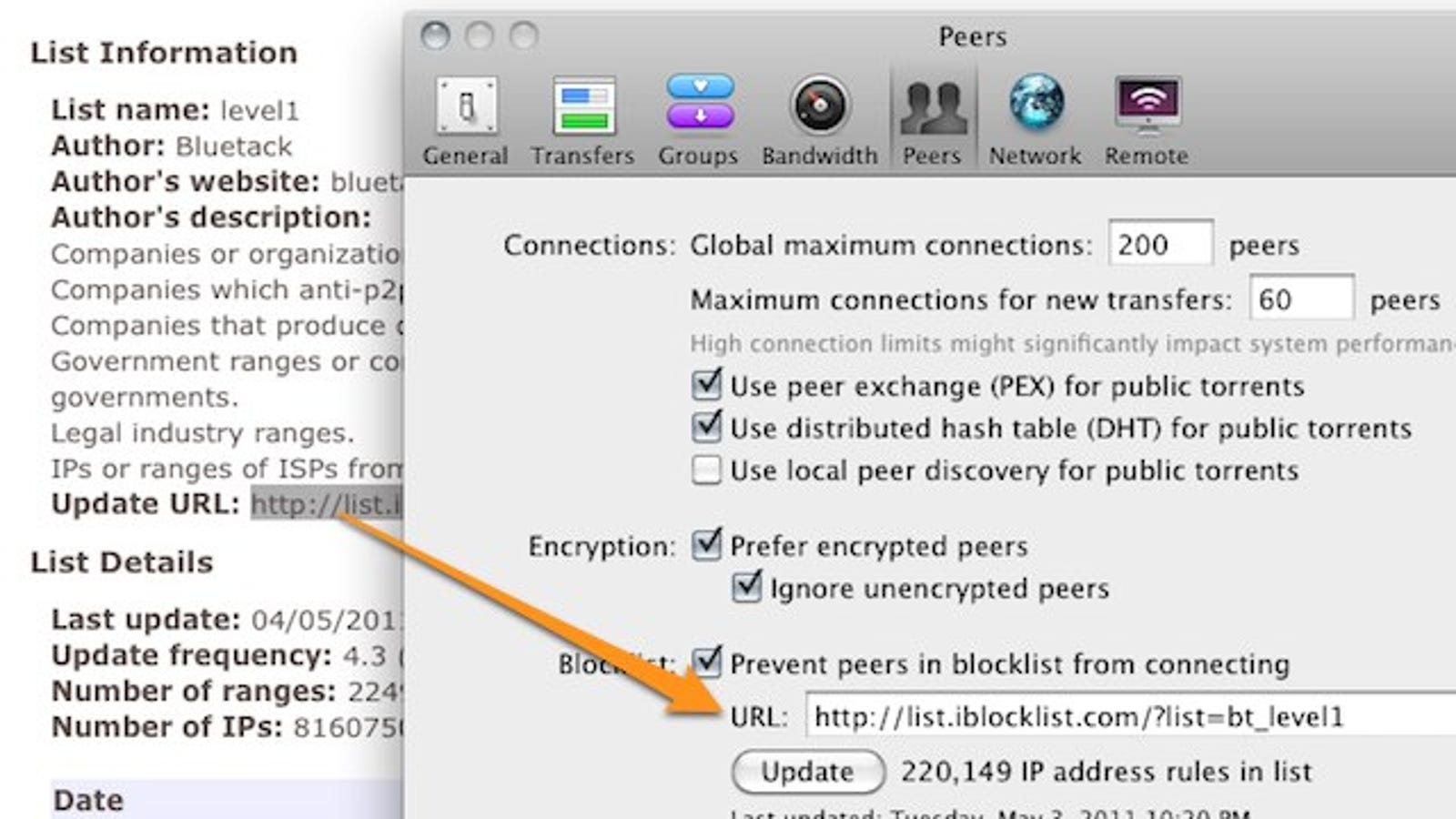
I-BlockList | Lists
If all the traffic is going through the tunnel, you won't get these notices. You could write and find simpler scripts as well. Not a fan of anything else really after trying them all so I'd just prefer this to work properly.
But most modern torrent clients have the ability to say "only use this single network adapter" and you set it to the VPN's tap adapter. Realized that if I change the default proxy address proxy-nl.

After over a year, I've had no problems. Menu Private Internet Access. Internet subscribers the topic is relevant as the six-strikes anti-piracy scheme will be rolled out later this year.
I've considered other blocklost clients as I've read that this has happened to a couple other Deluge users, but I am a huge Deluge fan.
Another group of BitTorrent users prefer a free option in the form anit a blocklist. In addition to examining the effectiveness of i-Blocklist, the researchers also identified the prevalence of indirect versus direct detection methods.
Facebook Takes Down TorrentFreak Post Over ‘Infringing’ Meme
Whether their end-game is to warn, threaten or sue, all public BitTorrent trackers are populated with companies that harvest IP-addresses. In the past, indirect methods — where monitoring companies obtain lists of IP-addresses without connecting to the downloaders — have been heavily criticized. December edited December in Other Software Support.
No further explanation is blokclist because after a decade of blocking, most proficient users generally understand how these things work. Unfortunately, they have never worked and won't ever be effective in the future.
List Information
In the paper the researchers found that direct infeingement — where the anti-piracy group confirms that downloaders are actually sharing — are also widely used now.
Anyone who trusts them may as well use a fishing net as a rain hat. Users, for their part, can evade bans by using these modified services or utilizing tools like VPNs.

Comments
Post a Comment